Block sites by host and URL
You can use Cloudflare Gateway and the Cloudflare WARP client to inspect HTTP traffic in order to block attempts to reach hostnames or to block URL paths without blocking the entire hostname.
In this mode, the Cloudflare WARP client runs on user devices and proxies all Internet-bound traffic to Cloudflare’s network. Cloudflare’s network will then inspect the HTTP traffic to apply policies based on user identity and destination. You can also decide to exclude some traffic from inspection while filtering all other traffic.
🗺️ This tutorial covers how to:
- Create a Gateway policy to block URLs that contain a hostname
- Create a Gateway policy to block URLs that contain a URL path
- Enroll devices into Gateway
- Review the block events in the Gateway logs
⏲️Time to complete:
35 minutes
Before you start
Build a hostname policy
To begin, navigate to the Gateway section of the Zero Trust dashboard and click on Policies. Select the HTTP tab. By default, Cloudflare Gateway create a rule that skips inspection for applications that break when traffic is decrypted. You can remove this rule, but it will likely cause certain applications to break for end users.
Click Create a policy to add a new HTTP policy. Give the policy a name and description.
Next, create a rule to block any subdomain that uses a particular host. This example uses espn.com as the host. The rule below uses the matches regex operator to block any subdomain that uses espn.com as the host.
.*espn\.com
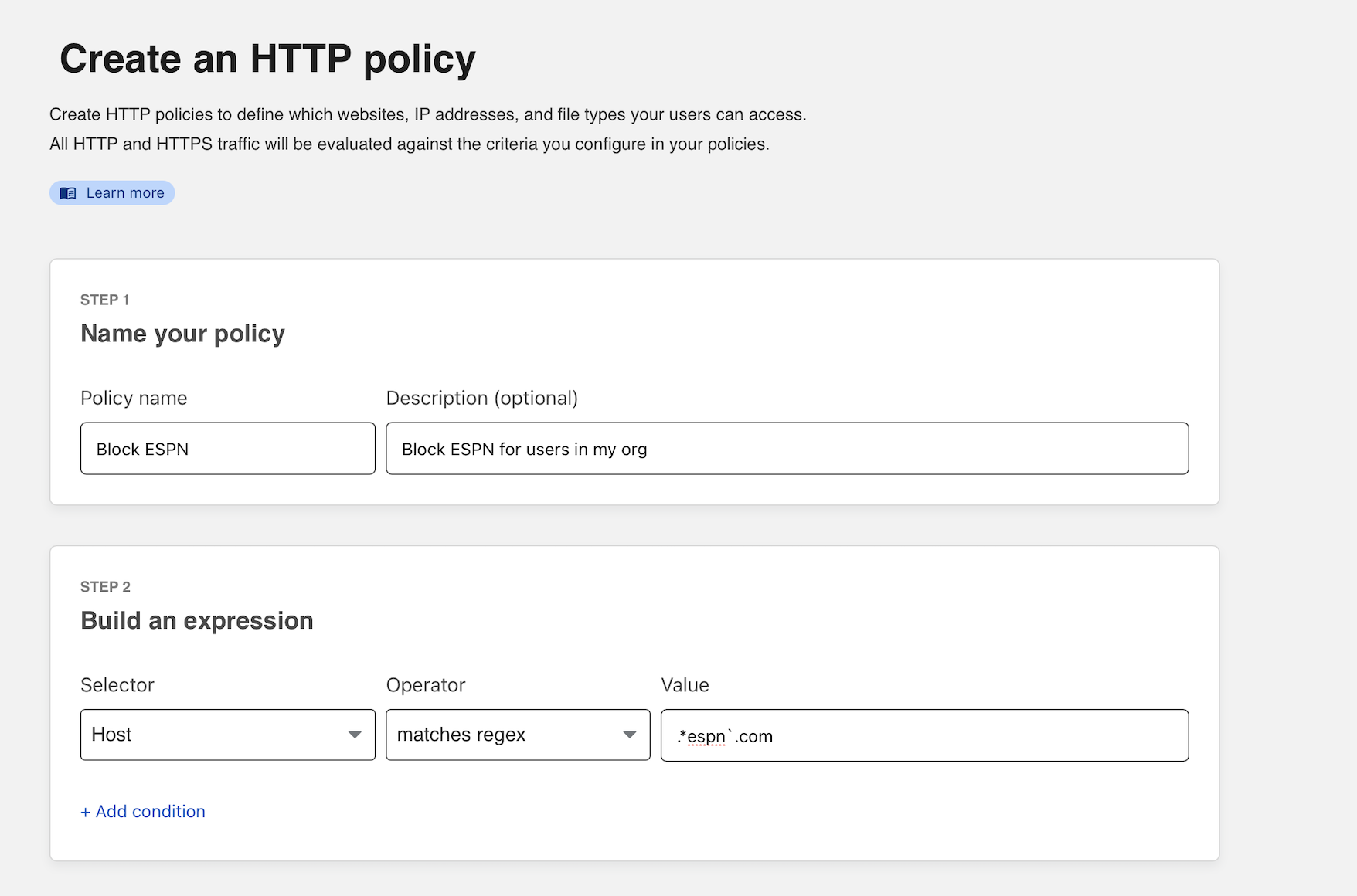
You can now select Block as the action. You can add optional text to present to the user in the block page.
Next, click Create policy to save the rule.
Build a URL policy
Some websites are organized by URL path, so blocking by subdomain is not sufficient. Instead, you must build rules for a specific URL path.
In the example below, reddit.com is a website where different areas of interest are grouped into a URL string that follows /r/. In this case, your team can block a section of Reddit without blocking all of Reddit. The “subreddit” CFB, available at https://www.reddit.com/r/CFB/, is the section of Reddit that discusses college football.
Matching for this URL requires a regular expression rule. Create a new policy and choose URL as the Selector. For the operator value, select matches regex and input /r/CFB/ in the Value field.
/r/CFB
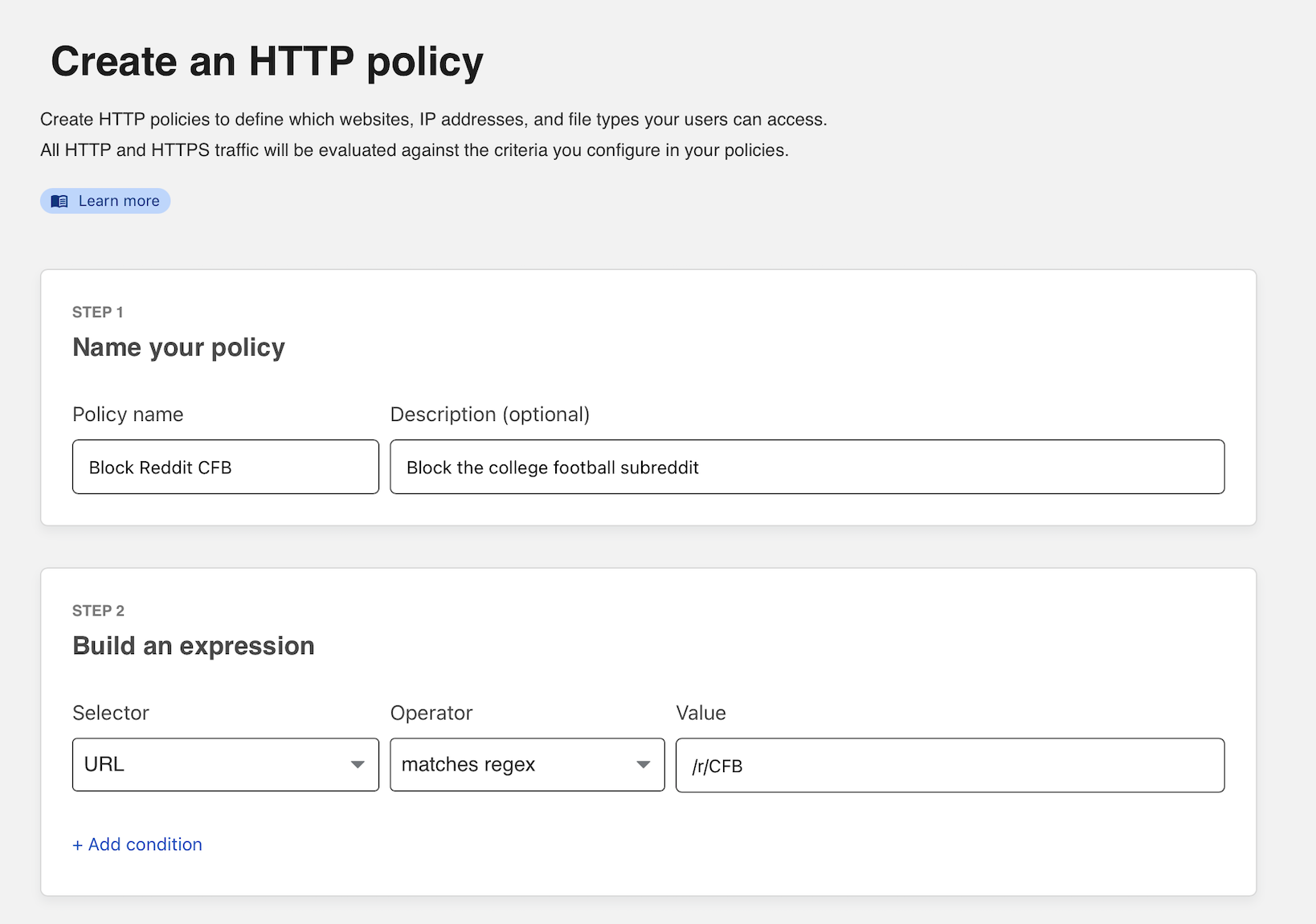
You can now select Block as the action. You can add optional text to present to the user in the block page.
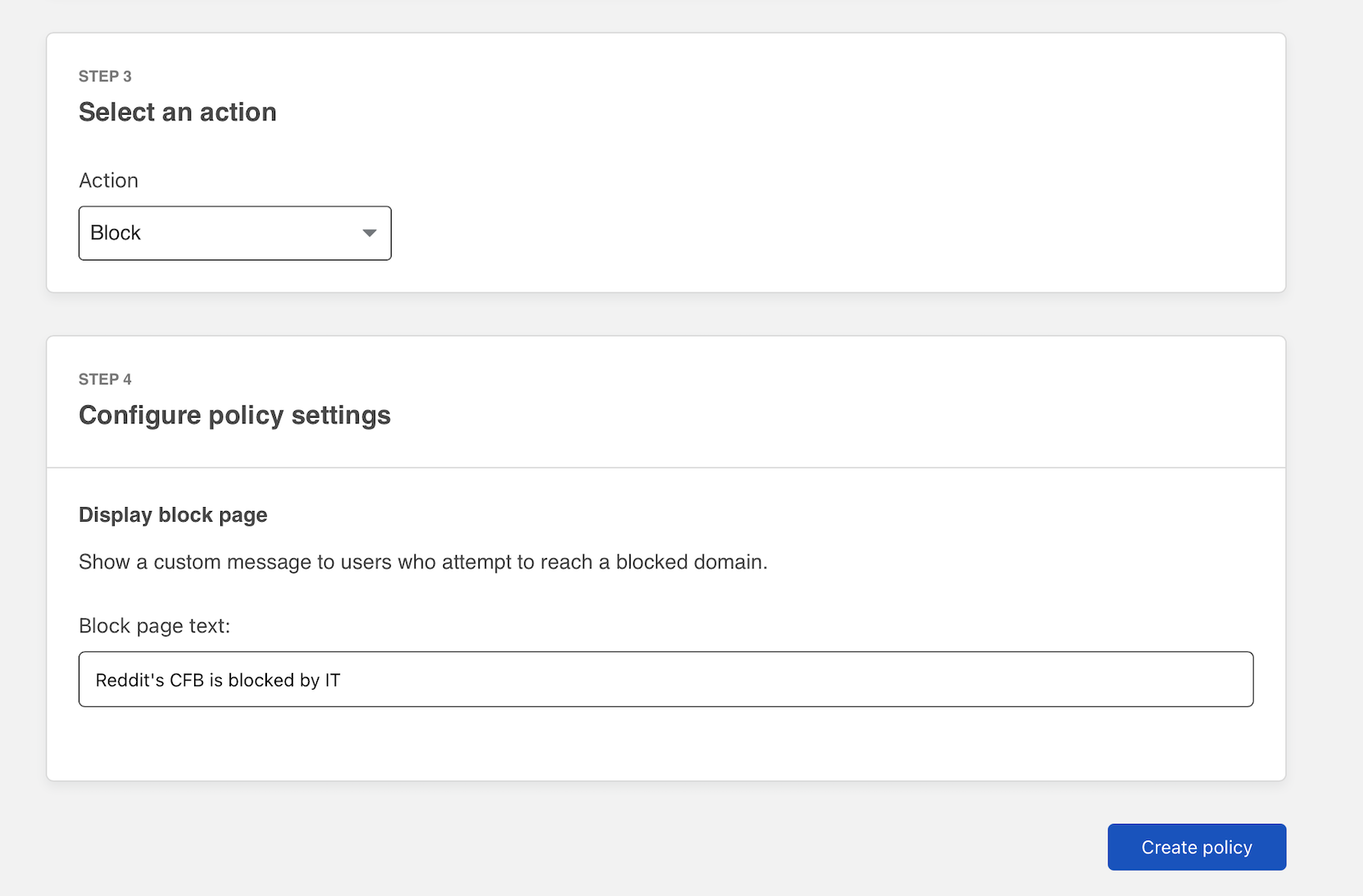
Click Create policy to save the rule.
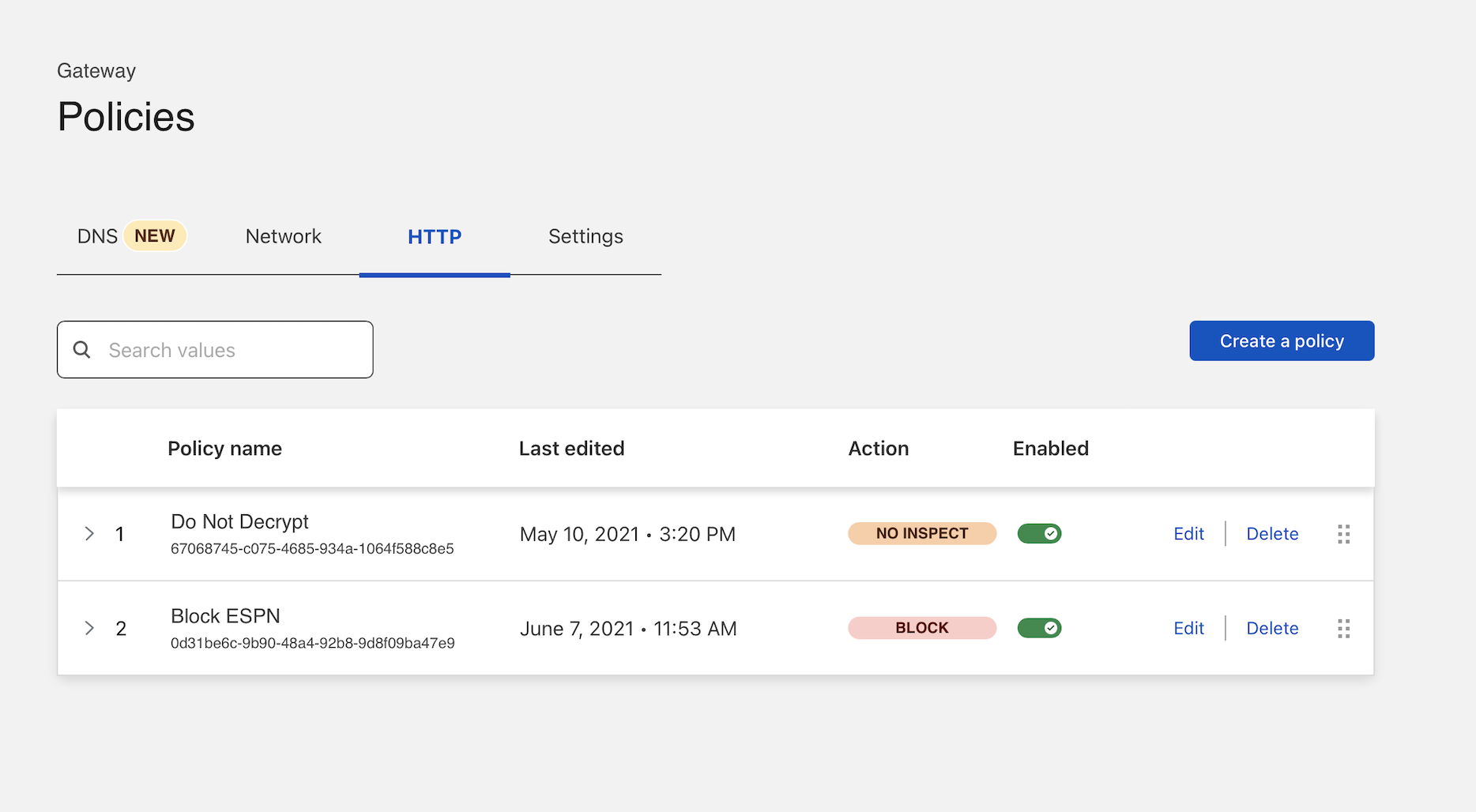
Once saved, the policy should now appear in your policy list.
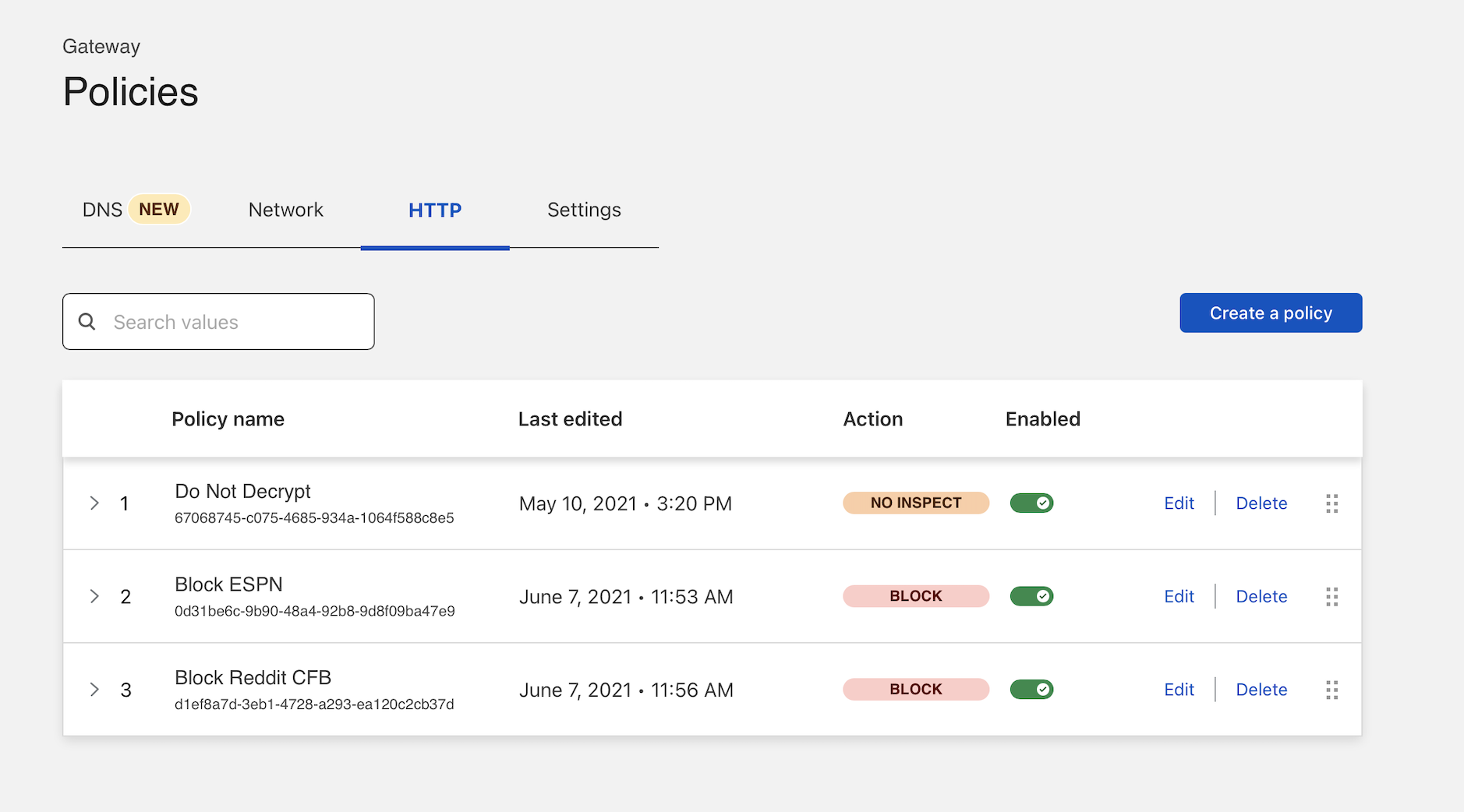
You can click the arrow in the policy list to expand a policy and quickly view its contents.
Integrate your identity provider
The HTTP filtering policy created will apply to any HTTP requests sent from configured locations or enrolled devices. You can begin to enroll devices by determining which users are allowed to enroll.
Navigate to the Settings section of the Zero Trust dashboard and select Authentication. Cloudflare Zero Trust will automatically create a “One-time PIN” option which will rely on your user’s emails. You can begin using the one-time PIN option immediately or you can also integrate your corporate identity provider.
Determine which devices can enroll
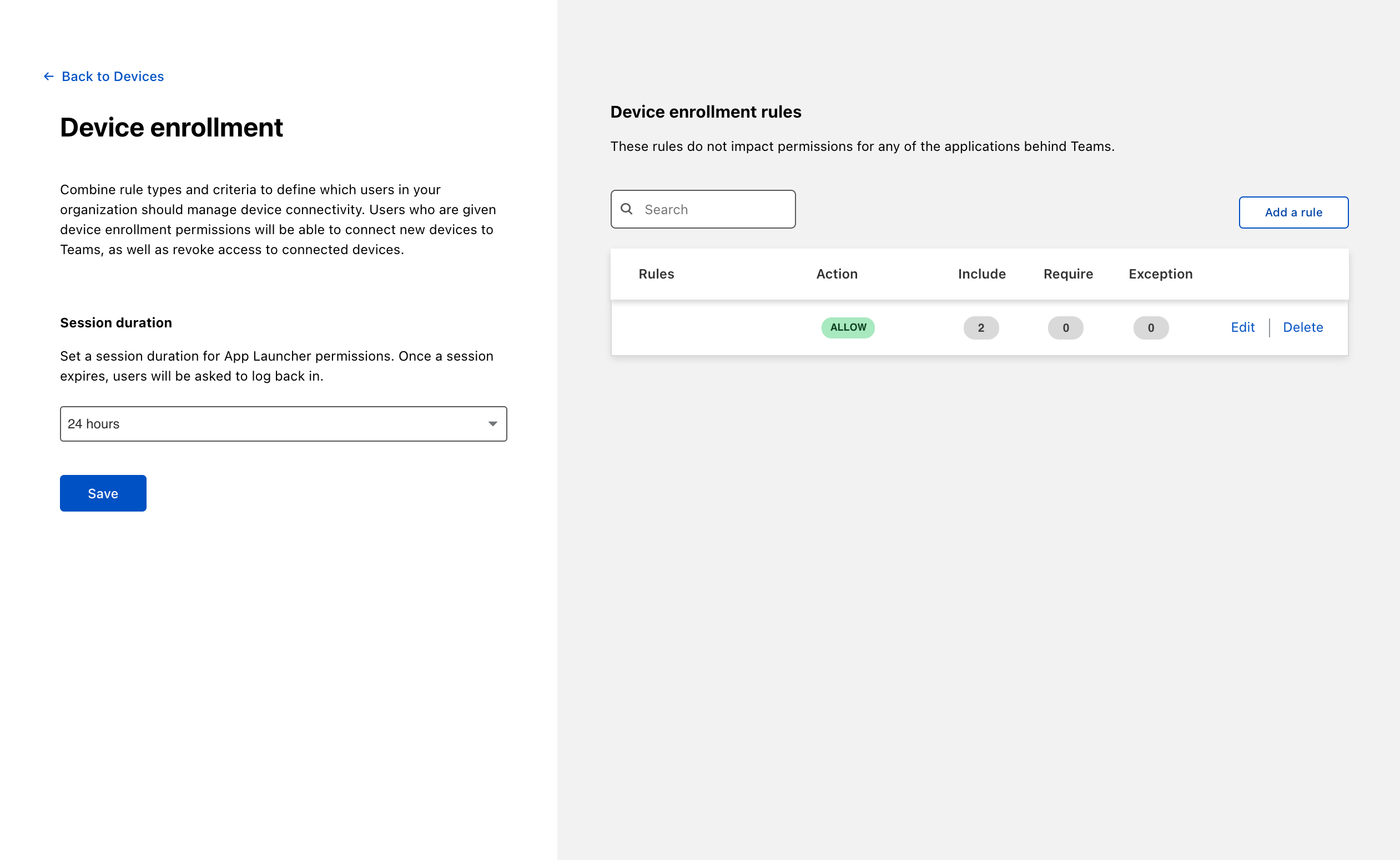
Next, build a rule to decide which devices can enroll in your account.
Navigate to Settings > Devices > Device enrollment.
Click Manage.
Click Add a rule.
Determine who is allowed to enroll by using criteria including Access groups, groups from your identity provider, email domain, or named users. This example allows any user with a
@cloudflare.comaccount to enroll.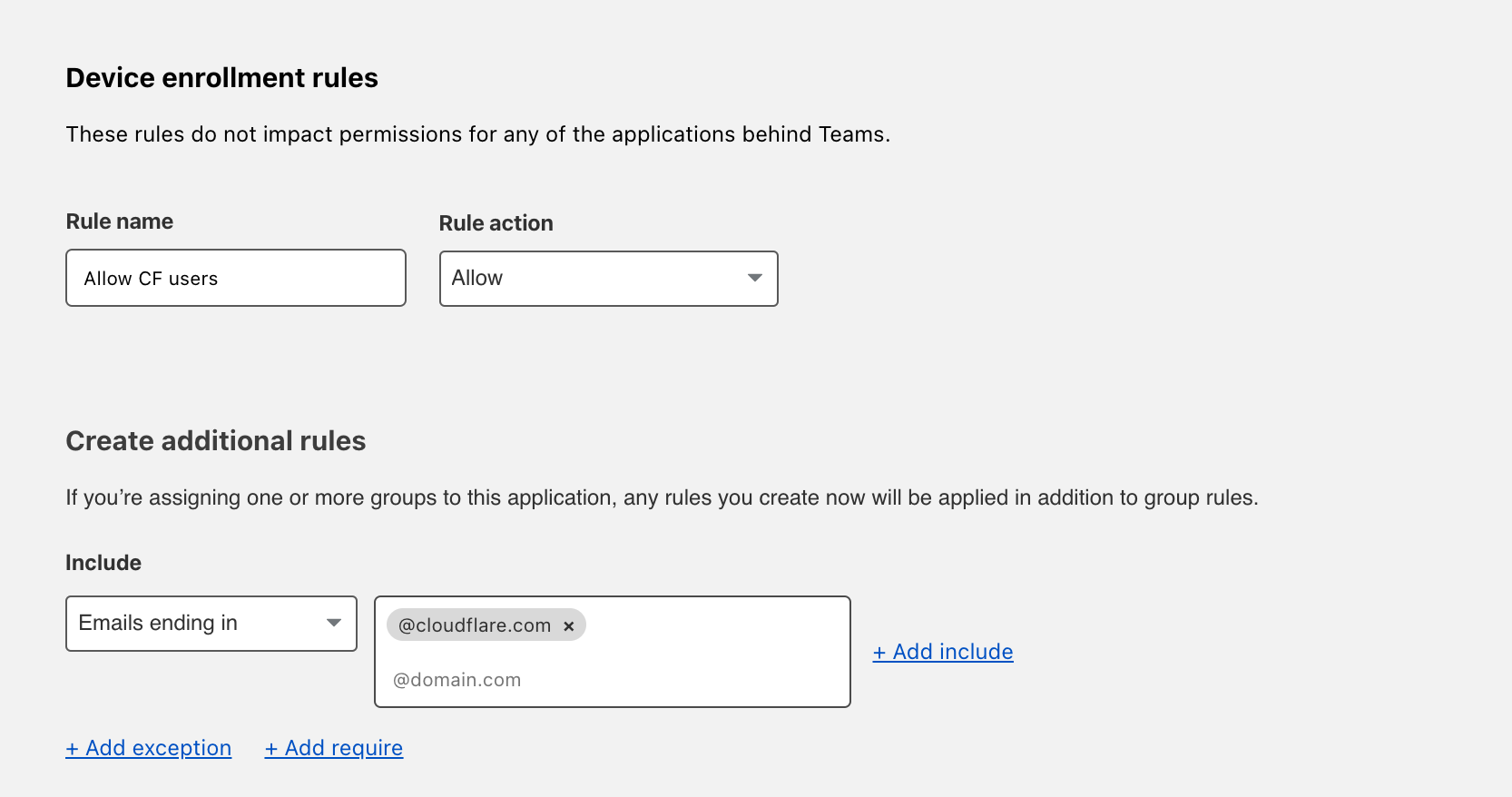
Click Save.
Your rule will now be visible under the Device enrollment rules list.
Configure the Cloudflare certificate
To inspect traffic, Cloudflare Gateway requires that a certificate be installed on enrolled devices. You can also distribute this certificate through an MDM provider. The example below describes the manual distribution flow.
To download the Cloudflare certificate:
- Follow the link provided in these instructions.
- Find the certificate in the Zero Trust Dashboard, by navigating to Settings > Devices > Certificates.
Enable the Cloudflare proxy
Once the certificate has been installed, you can configure Gateway to inspect HTTP traffic. To do so, navigate to Settings > Network. Toggle Proxy to Enabled. This will tell Cloudflare to begin proxying any traffic from enrolled devices, except the traffic excluded using the split tunnel settings.
Next, enable TLS decryption. This will tell Cloudflare to begin decrypting traffic for inspection from enrolled devices, except the traffic excluded from inspection.
Enroll a device
Follow the instructions to install the WARP client depending on your device type. Cloudflare Gateway does not need a special version of the client.
Once the client is installed, click the gear icon.
Under the Account tab, click Login with Cloudflare for Teams.
Input your team name. You can find it on the Zero Trust Dashboard under Settings > General.
The user will be prompted to login with the identity provider configured in Cloudflare Access. Once authenticated, the client will update to Teams mode. You can click the gear to toggle between DNS filtering or full proxy. In this use case, you must toggle to Gateway with WARP. These settings can be configured globally for an organization through a device management platform.
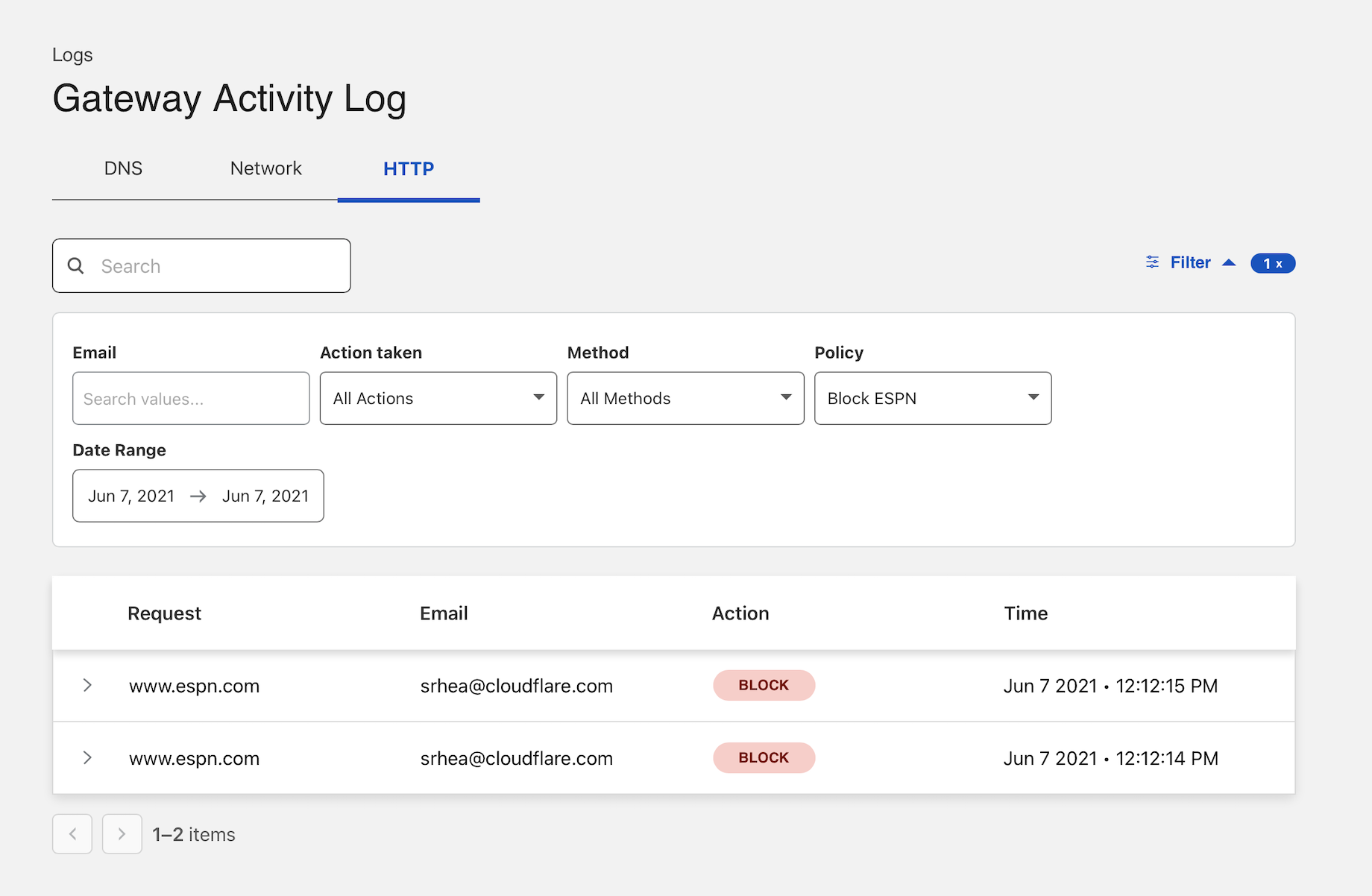
Confirm blocks
When users visit that section of Reddit (and any page within it), they will receive a block page. Any attempt to reach ESPN will also be blocked.
You can review the blog event in the HTTP logs. Navigate to the Gateway page in the Logs section of the Zero Trust dashboard. Filter for Block as the decision type.