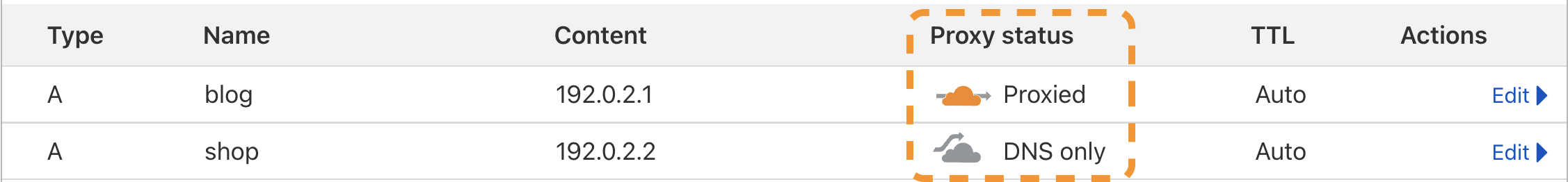
Proxy status
The Proxy status of a DNS record affects how Cloudflare treats incoming traffic to that record.
Cloudlare recommends enabling our proxy for all A, AAAA, and CNAME records.
Proxied records
When an A, AAAA, or CNAME record is Proxied — also known as being orange-clouded — DNS queries for these will resolve to Cloudflare Anycast IPs instead of their original DNS target. This means that all requests intended for proxied hostnames will go to Cloudflare first and then be forwarded to your origin server.
This behavior allows Cloudflare to optimize, cache, and protect all requests to your application, as well as protect your origin server from DDoS attacks.
Because requests to proxied hostnames go through Cloudflare before reaching your origin server, all requests will appear to be coming from Cloudflare’s IP addresses (and could potentially be blocked or rate limited). If you use proxied records, you may need to adjust your server configuration to allow Cloudflare IPs.
Limitations
Record types
By default, Cloudflare only supports proxied A, AAAA, and CNAME records. You cannot proxy other record types.
If you encounter a CNAME record that you cannot proxy — usually associated with another CDN provider — a proxied version of that record will cause connectivity errors. Cloudflare is purposely preventing that record from being proxied to protect you from a misconfiguration.
Ports and protocols
By default, Cloudflare only proxies HTTP and HTTPS traffic.
If you need to connect to your origin using a non-HTTP protocol (SSH, FTP, SMTP) or the traffic targets an unsupported port at the origin, either leave your records unproxied (DNS-only) or use Cloudflare Spectrum.
Pending domains
When you onboard your domain onto Cloudflare, Cloudflare protection will be in a pending state until we can verify ownership. This could take up to 24 hours to complete.
This means that DNS records - even those set to proxy traffic through Cloudflare – will be DNS-only until your zone has been activated and any requests to your DNS records will return your origin server’s IP address.
If this warning is still present after 24 hours, refer to our troubleshooting guide.
For enhanced security, we recommend rolling your origin IP addresses at your hosting provider after your zone has been activated. This action prevents your origin IPs from being leaked during onboarding.
Windows authentication
Because Microsoft Integrated Windows Authentication, NTLM, and Kerberos violate HTTP/1.1 specifications, they are not compatible with proxied DNS records.
To solve this issue, we recommend using Cloudflare Zero Trust.
DNS-only records
When an A, AAAA, or CNAME record is DNS-only — also known as being gray-clouded — DNS queries for these will resolve to the record’s normal IP address.
In addition to potentially exposing your origin IP addresses to bad actors and DDoS attacks, leaving your records as DNS-only means that Cloudflare cannot optimize, cache, and protect requests to your application.